Some years ago i had the chance to play around with one of these spycams:

It all started with a friend of mine who told me that his “smart” bulb was sending data to a bunch of strange ip addresses. That got me curious to check if of these cameras, which i borrowed from the IOT lab at the uni, can reveal some interesting stuff.
The first thing I’ve noticed is that the included android app for these cameras, can show the video feed without asking for credentials. Let’s see what wireshark intercepts

So by looking at the udp stream above, it was discovered that:
- The client (android app) sends the “8888” string to a high udp port of the camera (backdoor).
- Now the cam responds with a requests that contains the stored username and password and then the nearby wifi access points.
- After that the client asks for a H264 video stream and so on.
Looking at the traffic generated, i’ve noticed a strange behaviour:

It looks like that the spycam sends every now and then a braodcast requests with the stored credentials …and also a url to an adult website (?)
Anyway now that we received the admin credentials we can log inside the camera and do stuff.

Now back to the original question, i’ve found that this camera sends data to these ip addresses:
- 72.52.179.174 (some cloud provider, now unreachable)
- 35.205.61.67 (google cloud)
- 112.124.40.254 (again another provider, chinese this time, aliyun)
- 54.200.199.150 (amazon aws)
From what i’ve seen the data that was sent are just heartbeat messages:

And among those ip addresses, the only one that is still reachable is the amazon aws
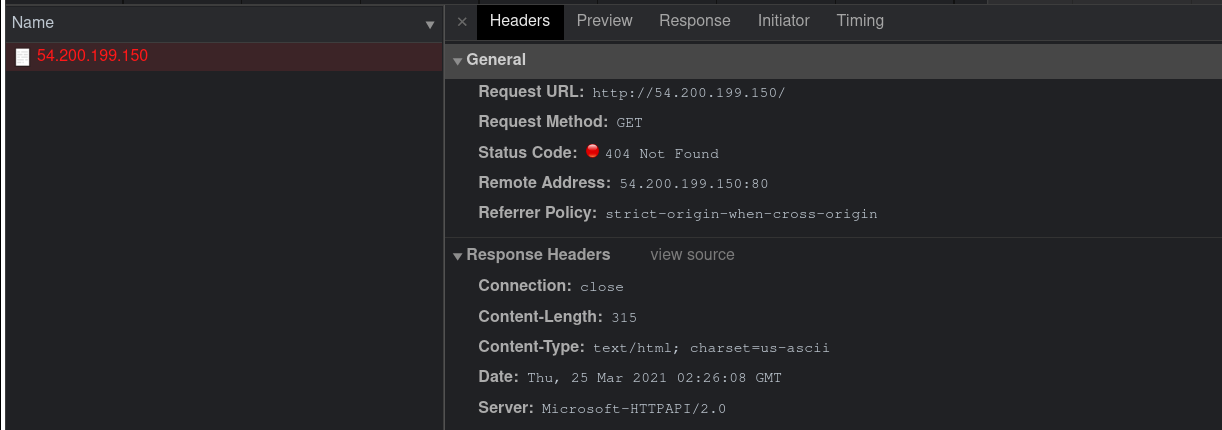
It runs with a httpapi/2.0 instance… but i’ve stopped here.
So there’s my quick investigation on these devices, sadly i can’t get my hands on these anymore, nowadays i would try to pwn the web interface, but at the time i wasn’t interested in cybsersec. Lessons learned:
- If you’ll ever find one of these devices, just use the 8888 backdoor pin on the udp port 57122, or just sniff the traffic and eventually you’ll see the credentials in clear.
- These cameras sends heartbeat via udp packages to some cloud instances, from the traffic i’ve seen there was no sensitive data transmitted, but i wouldn’t trust these cams
- For some reason an adult website url is sent among the credentials, I hope this doesn’t trigger anything on the android app (maybe the the developer put a backdoor to spy on the spycam?)
- Although these devices seems cheap and low quality, they are in fact quite expensive. So if someone is spying on you, and you don’t want to get into legal stuff, you’d better stole the thing and sell it on ebay (just kidding).